For the second time this year we participated to Pwn2Own where we demonstrated the exploitation of several impactful 0-day vulnerabilities.
This time, we joined the Pwn2Own Ireland 2024 event taking on a new challenge: the SOHO (Small Office/Home Office) smashup! This simulated a real-world attack scenario, starting from the external network side of a router to eventually breach and target devices within the local network.
Our targets were two devices manufactured by QNAP: the QHora-322 router and the popular TS-464 NAS.
During the event, our exploit ran with impressive speed—taking less than 15 seconds to gain full control over both devices. We demonstrated this by obtaining administrator access, blinking the LED and activating the bell on each device, and finally making some “old-school” alterations to the NAS’s admin panel to show that we’d achieved full access.
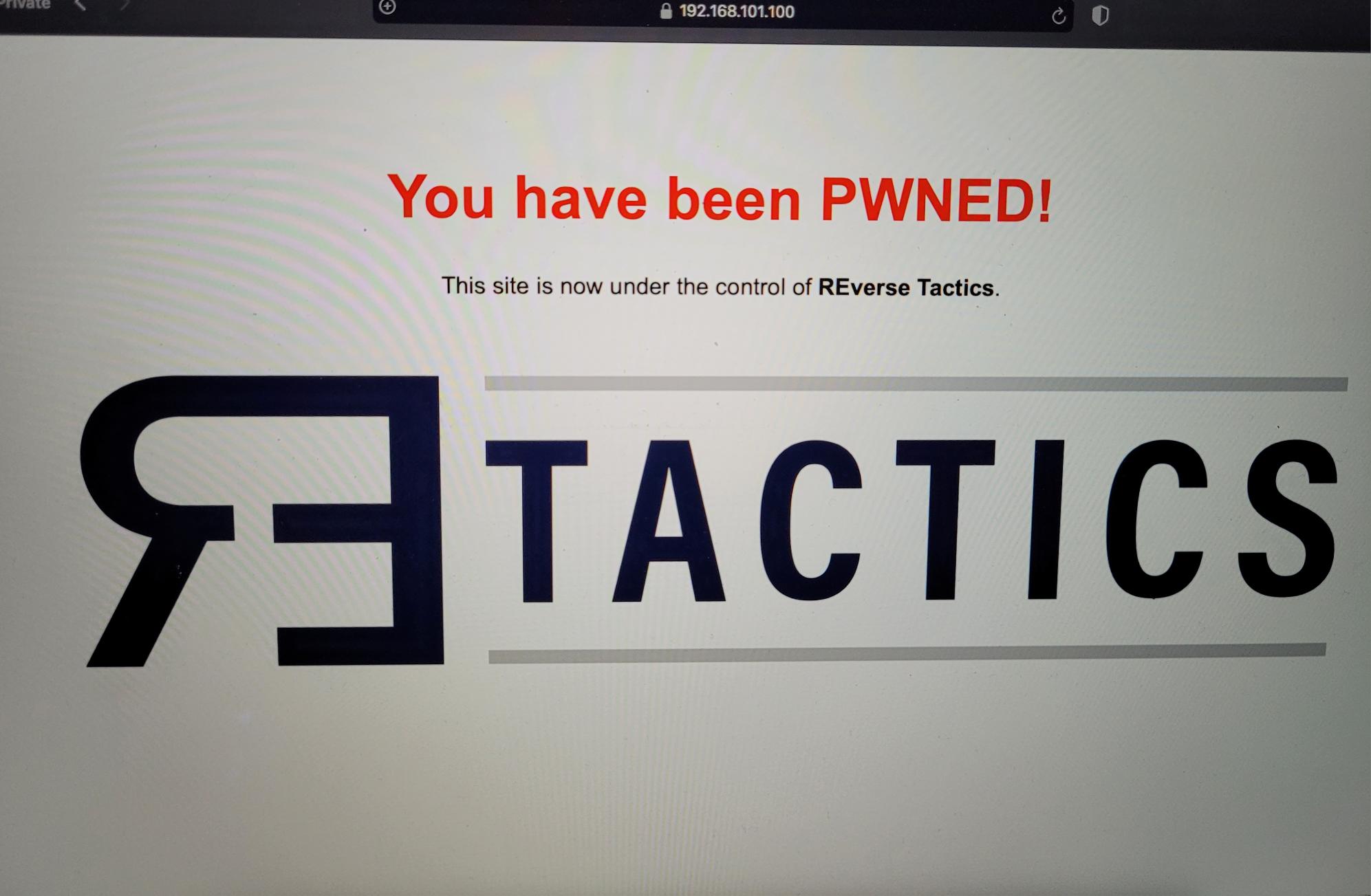
We’re currently collaborating with QNAP to help patch the vulnerabilities identified, ensuring enhanced security for their users.
At REverse Tactics, we bring extensive expertise in IoT security, capable of performing full audits of exposed surfaces on IoT devices. Our team excels at identifying high-impact vulnerabilities, demonstrating how real-world exploitation scenarios can unfold, and providing actionable insights to enhance device security.
A big thanks to Trend Micro’s Zero Day Initiative and QNAP for the opportunity to contribute to a more secure IoT landscape!